Jan 8
/
Cyber Reports
Cybersecurity: Lessons to learn from 2025
A New Era of Financial Cyber Threats
As digital transformation accelerates and open-source tools proliferate, cyberattacks have emerged as one of the most serious threats to global financial stability. Over the past year, increasingly sophisticated criminal groups armed with advanced technologies have targeted consumers, financial institutions, and entire industries. The value of data has never been higher, and the attack surface has never been wider.
This analysis deconstructs the most significant cybersecurity incidents 2025 has revealed. By examining the methods, impacts, and outcomes of these events, we can extract critical lessons for professionals in the financial sector. The year's key trends crystallized around three core themes: a record-setting state-sponsored crypto heist, a pervasive wave of vendor data breaches that underscored supply-chain risk, and the weaponization of artificial intelligence to perpetrate advanced fraud. These are not isolated events; they are calculated campaigns that reveal a strategic shift in how threat actors are targeting the global financial system.
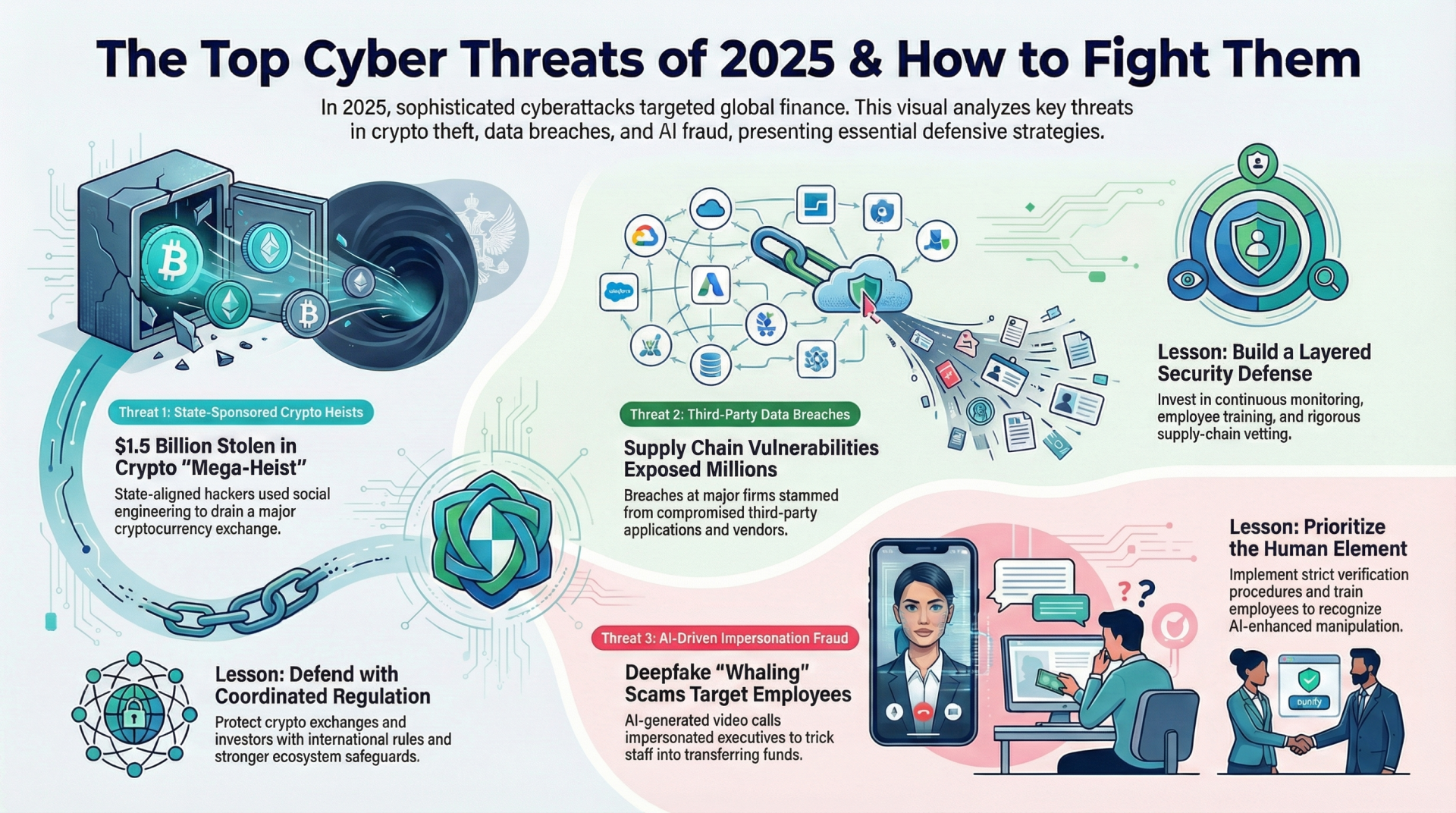
Case Study 1: The State-Sponsored Crypto Mega-Heist
The $1.5 Billion Heist that Shook the Crypto Markets
2025 set new records for financial theft, but one incident stood out for its sheer scale: the unprecedented breach of the Bybit cryptocurrency exchange. In February, attackers used social engineering tactics and exploited a third-party wallet provider to authorize a series of fraudulent transfers, ultimately draining approximately $1.5 billion in Ethereum from the platform.
The FBI later attributed the sophisticated operation to the Lazarus Group, a state-aligned North Korean threat actor known for its focus on financial cybercrime. The attack sent shockwaves through the crypto markets and reignited urgent global debates around the need for comprehensive regulatory oversight of the digital asset industry.
Actionable Insight: This incident demonstrates that modern cybercrime has evolved into a highly organized, well-funded global industry, often with the direct support of nation-state actors. Cross-border crypto theft is especially difficult to investigate due to the ease of laundering digital assets. Protecting exchanges and investors will require coordinated international regulation, stronger transparency requirements, and more robust technical safeguards across the entire crypto ecosystem.
Case Study 2: The Pervasive Threat of Supply-Chain Data Breaches
A Wave of Breaches Highlights Supply-Chain Vulnerabilities
Data exposure resulting from third-party compromises was a defining cybersecurity challenge in 2025. Attackers increasingly targeted vendors and service providers as a means to access the sensitive information held by major financial institutions. These data breaches 2025 highlighted the systemic risks inherent in a deeply interconnected digital supply chain.
• LexisNexis (29 May 2025): A third-party compromise exposed the personal information of more than 364,000 individuals, including contact details, Social Security numbers, and driver’s license information. The company engaged external cybersecurity specialists and notified law enforcement.
• TransUnion (28 August 2025): A breach affecting over 4 million consumers stemmed from a vulnerable third-party application used in the company's U.S. customer support operations.
• Wealthsimple (9 September 2025): Attackers accessed personal and financial data such as account numbers, government IDs, and IP addresses for less than 1% of the firm’s three million customers. No funds or passwords were compromised.
Actionable Insight: Attackers are innovating their tactics and tools faster than many organizations can adapt their defenses. Robust financial sector cybersecurity is no longer achievable through perimeter security alone. It requires a layered defense strategy encompassing strong authentication, continuous monitoring, and comprehensive data encryption. Critically, it demands rigorous vetting and oversight of all supply-chain partners, which includes demanding SOC 2 Type II compliance, conducting penetration tests on integrated APIs, and contractually mandating immediate breach notification.
Case Study 3: The Rise of AI-Powered Impersonation and Fraud
Deepfakes and Whaling: When Seeing Is No Longer Believing
Artificial intelligence became a dual-use technology in 2025. While financial institutions expanded AI for fraud detection and operational efficiency, cybercriminals leveraged deep learning to generate convincing synthetic audio, video, and text. These "deepfakes" enabled a significant surge in sophisticated impersonation and deepfake scams.
The most damaging of these attacks involved "whaling," a technique where threat actors use deepfake video calls to impersonate senior executives. The goal is to trick employees into authorizing large, fraudulent fund transfers or disclosing sensitive corporate data. In March, Singaporean authorities issued a public warning about a spike in such scams, noting that criminals were using platforms like WhatsApp and Zoom to initiate contact and conduct these highly convincing impersonations.
Actionable Insight: Technology can create new vulnerabilities, but human behavior often remains the weakest link in the security chain. Social engineering, especially when enhanced by convincing AI, can bypass even strong technical controls. Organizations must implement strict, multi-channel verification procedures for all financial requests and develop robust, ongoing training programs to help employees recognize the hallmarks of AI-enhanced manipulation.
Evolving Threats, Evolving Defenses: Key Priorities for 2026
Digitization has removed geographic barriers for criminals, allowing them to target financial entities anywhere in the world with minimal effort. With powerful attack tools widely accessible on the black market and stolen data more valuable than ever, every layer of the financial ecosystem—from central banks to vendors to individual consumers—is at risk.
Addressing this complex threat landscape requires a multi-layered and proactive response. The incidents of 2025 point to several clear priorities for building a more resilient financial system:
• Stronger and more harmonized crypto regulation across jurisdictions.
• Deeper investment in advanced cybersecurity capabilities, from threat intelligence to incident response.
• Improved and continuous education for both consumers and employees on emerging threats.
• Rigorous and ongoing third-party and supply-chain risk management and oversight.
A recurring theme across 2025's major incidents was the critical reliance on external expertise to contain the fallout. While emergency response is vital, the strategic lesson is clear: organizations can no longer afford to outsource their core resilience. To safeguard data and maintain financial stability against the backdrop of the cybersecurity incidents 2025 has shown us, organizations must treat cyber resilience as a core operational priority and commit to building the in-house cybersecurity talent capable of defending against the sophisticated threats of tomorrow.
As digital transformation accelerates and open-source tools proliferate, cyberattacks have emerged as one of the most serious threats to global financial stability. Over the past year, increasingly sophisticated criminal groups armed with advanced technologies have targeted consumers, financial institutions, and entire industries. The value of data has never been higher, and the attack surface has never been wider.
This analysis deconstructs the most significant cybersecurity incidents 2025 has revealed. By examining the methods, impacts, and outcomes of these events, we can extract critical lessons for professionals in the financial sector. The year's key trends crystallized around three core themes: a record-setting state-sponsored crypto heist, a pervasive wave of vendor data breaches that underscored supply-chain risk, and the weaponization of artificial intelligence to perpetrate advanced fraud. These are not isolated events; they are calculated campaigns that reveal a strategic shift in how threat actors are targeting the global financial system.
Case Study 1: The State-Sponsored Crypto Mega-Heist
The $1.5 Billion Heist that Shook the Crypto Markets
2025 set new records for financial theft, but one incident stood out for its sheer scale: the unprecedented breach of the Bybit cryptocurrency exchange. In February, attackers used social engineering tactics and exploited a third-party wallet provider to authorize a series of fraudulent transfers, ultimately draining approximately $1.5 billion in Ethereum from the platform.
The FBI later attributed the sophisticated operation to the Lazarus Group, a state-aligned North Korean threat actor known for its focus on financial cybercrime. The attack sent shockwaves through the crypto markets and reignited urgent global debates around the need for comprehensive regulatory oversight of the digital asset industry.
Actionable Insight: This incident demonstrates that modern cybercrime has evolved into a highly organized, well-funded global industry, often with the direct support of nation-state actors. Cross-border crypto theft is especially difficult to investigate due to the ease of laundering digital assets. Protecting exchanges and investors will require coordinated international regulation, stronger transparency requirements, and more robust technical safeguards across the entire crypto ecosystem.
Case Study 2: The Pervasive Threat of Supply-Chain Data Breaches
A Wave of Breaches Highlights Supply-Chain Vulnerabilities
Data exposure resulting from third-party compromises was a defining cybersecurity challenge in 2025. Attackers increasingly targeted vendors and service providers as a means to access the sensitive information held by major financial institutions. These data breaches 2025 highlighted the systemic risks inherent in a deeply interconnected digital supply chain.
• LexisNexis (29 May 2025): A third-party compromise exposed the personal information of more than 364,000 individuals, including contact details, Social Security numbers, and driver’s license information. The company engaged external cybersecurity specialists and notified law enforcement.
• TransUnion (28 August 2025): A breach affecting over 4 million consumers stemmed from a vulnerable third-party application used in the company's U.S. customer support operations.
• Wealthsimple (9 September 2025): Attackers accessed personal and financial data such as account numbers, government IDs, and IP addresses for less than 1% of the firm’s three million customers. No funds or passwords were compromised.
Actionable Insight: Attackers are innovating their tactics and tools faster than many organizations can adapt their defenses. Robust financial sector cybersecurity is no longer achievable through perimeter security alone. It requires a layered defense strategy encompassing strong authentication, continuous monitoring, and comprehensive data encryption. Critically, it demands rigorous vetting and oversight of all supply-chain partners, which includes demanding SOC 2 Type II compliance, conducting penetration tests on integrated APIs, and contractually mandating immediate breach notification.
Case Study 3: The Rise of AI-Powered Impersonation and Fraud
Deepfakes and Whaling: When Seeing Is No Longer Believing
Artificial intelligence became a dual-use technology in 2025. While financial institutions expanded AI for fraud detection and operational efficiency, cybercriminals leveraged deep learning to generate convincing synthetic audio, video, and text. These "deepfakes" enabled a significant surge in sophisticated impersonation and deepfake scams.
The most damaging of these attacks involved "whaling," a technique where threat actors use deepfake video calls to impersonate senior executives. The goal is to trick employees into authorizing large, fraudulent fund transfers or disclosing sensitive corporate data. In March, Singaporean authorities issued a public warning about a spike in such scams, noting that criminals were using platforms like WhatsApp and Zoom to initiate contact and conduct these highly convincing impersonations.
Actionable Insight: Technology can create new vulnerabilities, but human behavior often remains the weakest link in the security chain. Social engineering, especially when enhanced by convincing AI, can bypass even strong technical controls. Organizations must implement strict, multi-channel verification procedures for all financial requests and develop robust, ongoing training programs to help employees recognize the hallmarks of AI-enhanced manipulation.
Evolving Threats, Evolving Defenses: Key Priorities for 2026
Digitization has removed geographic barriers for criminals, allowing them to target financial entities anywhere in the world with minimal effort. With powerful attack tools widely accessible on the black market and stolen data more valuable than ever, every layer of the financial ecosystem—from central banks to vendors to individual consumers—is at risk.
Addressing this complex threat landscape requires a multi-layered and proactive response. The incidents of 2025 point to several clear priorities for building a more resilient financial system:
• Stronger and more harmonized crypto regulation across jurisdictions.
• Deeper investment in advanced cybersecurity capabilities, from threat intelligence to incident response.
• Improved and continuous education for both consumers and employees on emerging threats.
• Rigorous and ongoing third-party and supply-chain risk management and oversight.
A recurring theme across 2025's major incidents was the critical reliance on external expertise to contain the fallout. While emergency response is vital, the strategic lesson is clear: organizations can no longer afford to outsource their core resilience. To safeguard data and maintain financial stability against the backdrop of the cybersecurity incidents 2025 has shown us, organizations must treat cyber resilience as a core operational priority and commit to building the in-house cybersecurity talent capable of defending against the sophisticated threats of tomorrow.
Executive IT Forums, Inc.
Educational Programs on Information Technology, Governance, Risk Management, & Compliance (GRC).

Our Newsletter
Get regular updates on CPE programs, news, and more.
Thank you!
Copyright © 2026 Executive IT Forums, Inc. All Rights Reserved.
Get started
Let us introduce our school
Write your awesome label here.