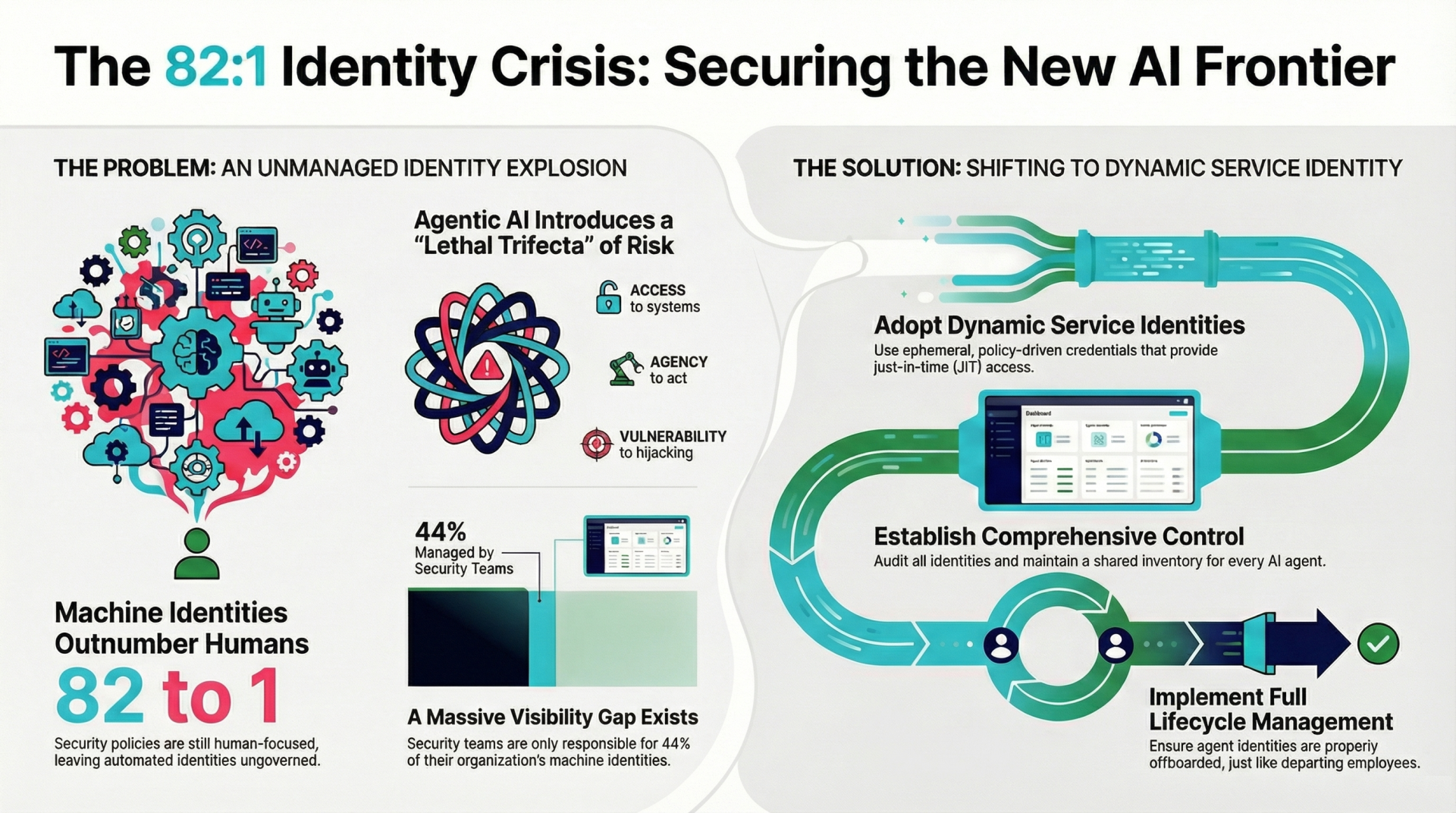
The traditional foundation of digital security, built on models like Active Directory and LDAP, is failing as it faces a new reality: machine identities now outnumber human users by a staggering 82 to 1. Originally designed for humans who log in and out, these legacy identity systems are unable to keep pace with the explosive growth of AI agents, which do not just authenticate but act autonomously. As ServiceNow’s $11.6 billion investment in security acquisitions throughout 2025 suggests, the primary control plane for enterprise risk has shifted from the AI models themselves to the identities that govern what those models can actually do.
Research from CyberArk and Gartner highlights a dangerous governance gap, noting that while machine identities dominate the landscape, 88% of organizations still only classify humans as "privileged users." This disconnect has resulted in machine identities frequently possessing higher levels of sensitive access than their human counterparts. The problem is compounded by a lack of visibility, with IAM teams typically managing less than half of an organization’s machine identities. This leaves a vast "shadow" ecosystem of API keys and service accounts that operate outside of security oversight, often persisting long after the workloads they supported have vanished.
The rise of agentic AI introduces a layer of complexity that legacy architectures were never intended to handle. These agents often utilize delegated human credentials or move across data silos using protocols like the Model Context Protocol (MCP), which frequently lacks built-in authentication. When agents spawn sub-agents or traverse internal tools, they collapse traditional identity boundaries, making it nearly impossible for security teams to maintain an auditable trail. Without a stable identity surface, these agents can move at machine speed, turning minor misconfigurations into systemic breaches before a human defender can intervene.
Attackers have already pivoted to exploit this shift, moving away from hardened endpoints to target long-lived, abandoned credentials. Security leaders note that it is far easier for an adversary to log in as an authorized admin using a forgotten service account than to bypass sophisticated endpoint protections. In several major enterprise breaches, the entry point was not a flaw in the AI itself, but a reused API key tied to an orphaned automation workflow. This "identity-first" attack strategy allows hackers to operate unconstrained within the cloud environment by simply masquerading as a legitimate, albeit non-human, user.
To combat this, Gartner recommends a transition toward "dynamic service identities" that are ephemeral, policy-driven, and tightly scoped. By moving away from static credentials toward just-in-time access, organizations can drastically reduce their attack surface and eliminate standing privileges. This approach requires a fundamental cultural shift where security teams and AI builders collaborate to maintain a shared registry of every agent’s ownership and permissions. Integrating automatic secret rotation and behavioral baselines into the development pipeline ensures that zero-trust principles are applied at the same speed at which the AI is deployed.
As we move through 2026, the gap between AI deployment and security governance is expected to widen. The 82-to-1 ratio of machines to humans is accelerating, and organizations relying on human-centric security models are accumulating dangerous levels of technical debt. Agentic AI breaks security not through its intelligence, but through its ability to multiply identity faster than traditional governance can follow. Surviving this new era requires acknowledging that perimeter-based security is no match for the scale and velocity of machine-on-machine attacks that have become the new corporate normal.